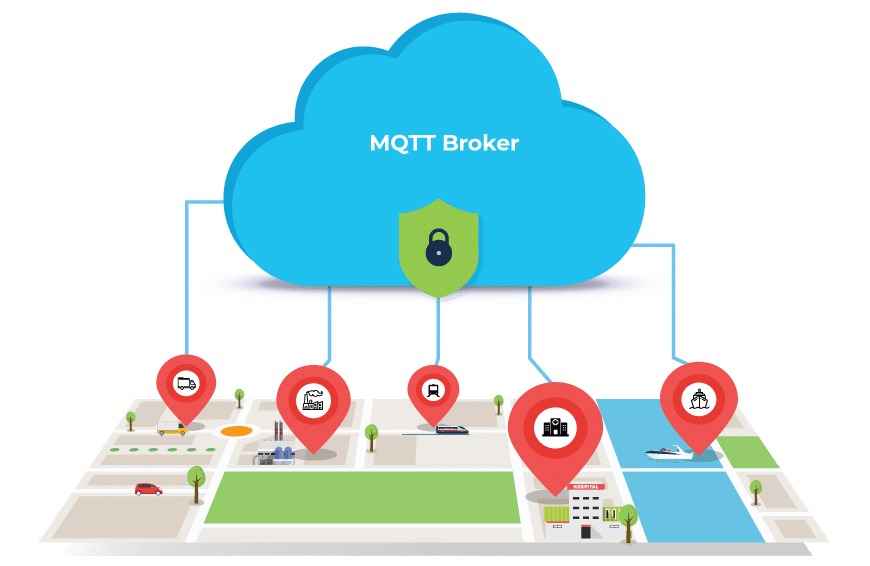
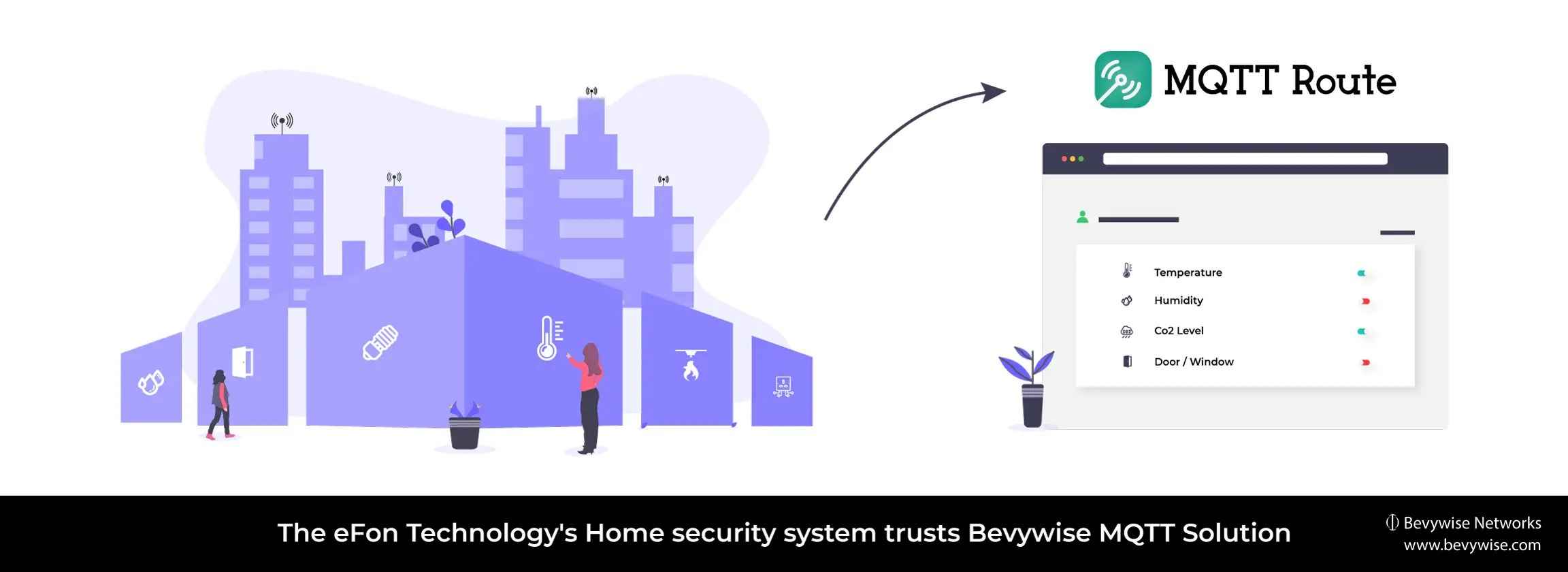
What is MQTT Security?
MQTT Security encompasses the practices, protocols, and technologies designed to safeguard IoT data transmitted using the MQTT (Message Queuing Telemetry Transport) protocol. As a lightweight and widely adopted protocol in IoT/IIoT implementations, ensuring the security of data transmitted via MQTT is crucial. By implementing robust MQTT security, organizations can prevent unauthorized access, data breaches, and other potential threats in their IoT ecosystems, ensuring the reliable and secure operation of their connected devices.